Please do not delegate the simple task of asking ChatGPT to forum members.
Here is another answer that ChatGPT could have give to you as well:
Short answer:
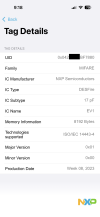
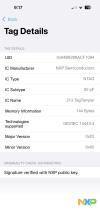
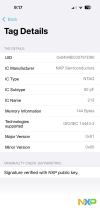
No, you cannot reliably read the unique ID (UID) of a MIFARE DESFire tag on iOS.
And here is the precise, formal explanation:
---
iOS does not expose the NFC tag UID for security and privacy reasons.
Apple intentionally blocks UID access except in a few very narrow cases.
For MIFARE DESFire, this means:
• The UID is completely hidden.
• iOS will never return it through Core NFC.
• Even with ISO-DEP (ISO 14443-4) sessions, you cannot retrieve the UID.
The only exception Apple makes is for NFC Forum Type-2 tags (NTAG, Ultralight C).
And even there, the UID is only partially exposed.
Because DESFire operates as an ISO-DEP smartcard, iOS treats it like a secure credential and blocks UID access entirely.
---
WHY APPLE BLOCKS UID ACCESS
Apple does this for privacy and anti-tracking reasons:
• A tag UID is globally unique and cannot be changed.
• If apps could read UIDs, they could track users across locations.
• Therefore, iOS requires that apps read only application data, not the hardware identity.
DESFire chips, being secure microcontrollers, fall under the “protected” category.
---
WHAT YOU CAN READ ON IOS FROM A DESFIRE TAG
iOS can:
• Open an ISO-DEP session
• Exchange APDUs with the DESFire application
• Read NDEF if the tag is formatted as a Type-4 Tag
• Access custom files if your app implements the full DESFire protocol
(and you have the keys)
But you will never get:
• UID
• ATS (Answer To Select, partially hidden)
• any hardware fingerprint
---
WORKAROUND: APPLICATION-LEVEL IDENTIFIER
Because you cannot read the UID, most iOS apps use:
1. an app-generated identifier written into a DESFire file, or
2. the DESFire internal serial number file (not the UID), or
3. a cryptographically signed challenge-response protocol (best practice)
This is the method used in:
• access control systems
• ticketing
• campus cards
• secure e-wallets
---
SUMMARY
DESFire + iOS:
• UID:

Not accessible
• NDEF: ✔ If T4T formatted
• ISO-DEP APDUs: ✔ Fully supported
• Custom DESFire apps: ✔ Yes
• Tracking-sensitive identifiers:

Blocked by Apple